Как удалить вирус?
Для начала патчи для виндовз поставь
И пароль администратора позаковыристее
И пароль администратора позаковыристее
это все есть
при сканировании нортон че нить в памяти находит? если находит но не может удалить, попробуй перегрузиться в сэйфмоде и оттуда просканиться
нет, не находит, хотя есть подозрения что это IEXPLOER.EXE (именно большими буквами).
Впрочем, остановка этого процесса не помогает.
Впрочем, остановка этого процесса не помогает.
Убей из автозапуска все, что ты не знаешь, что это такое.
именно ты угадал
вообще зайди на trendmicro.com и почитай описание виря
вообще зайди на trendmicro.com и почитай описание виря
у меня инет не работает к сожалению
не помогает
Solution:
AUTOMATIC REMOVAL INSTRUCTIONS
To automatically remove this malware from your system, please refer to the Trend Micro Damage Cleanup Engine and Template.
MANUAL REMOVAL INSTRUCTIONS
Identifying the Malware Program
To remove this malware, first identify the malware program.
Scan your system with your Trend Micro antivirus product.
NOTE all files detected as WORM_LOVGATE.G.
Trend Micro customers must download the latest pattern file before scanning their system. Other Internet users may use Housecall, Trend Micro’s free online virus scanner.
Terminating the Malware Program
This procedure terminates the running malware process from memory. If the process name is not known, you will need the name(s) of the file(s) detected earlier.
Open Windows Task Manager.
On Windows 95/98/ME systems, press
CTRL+ALT+DELETE
On Windows NT/2000/XP systems, press
CTRL+SHIFT+ESC, then click the Processes tab.
In the list of running programs*, locate the malware file or files detected earlier.
Select the file, then press either the End Task or the End Process button (depending on the version of Windows on your system).
Do the same for all detected malware files in the list of running processes.
To check if the malware process has been terminated, close Task Manager, and then open it again.
(Terminating an instance of the malware will also launch an instance of IEXPLORE.EXE. Terminate all other instances first before terminating IEXPLORE.EXE.)
Close Task Manager.
*NOTE: On systems running Windows 95/98/ME, Task Manager may not show certain processes. You may use a third party process viewer to terminate the malware process. Otherwise, continue with the next procedure, noting additional instructions.
Removing Autostart Entries from the Registry
Removing autostart entries from the registry prevents the malware from executing during startup.
Open Registry Editor. To do this, click Start>Run, type REGEDIT, then press Enter.
In the left panel, double-click the following:
HKEY_LOCAL_MACHINE>Software>Microsoft>Windows>
CurrentVersion>Run
In the right panel, locate and delete the following entries:
WinHelp = "C:\WINNT\System32\WinHelp.exe"
WinGate initialize = "C:\WINNT\System32\WinGate.exe -remoteshell"
Remote Procedure Call Locator = "RUNDLL32.EXE reg678.dll ondll_reg"
Program In Windows = "C:\WINNT\System32\IEXPLORE.EXE"
In the left panel, double-click the following:
HKEY_CURRENT_USER>Software>Microsoft>WindowsNT>
CurentVersion>Windows
In the right panel, locate and delete the following entry:
Run = ”RAVMOND.EXE”
Addressing Registry Shell Spawning
Registry shell spawning executes the malware when a user tries to run an .TXT file. The following procedures should restore the registry to its original settings.
Still in Registry Editor, in the left panel, double-click the following:
HKEY_CLASSES_ROOT>txtfile>shell>open>command
In the right panel, locate the registry entry:
Default
Check whether its data (in the rightmost column) is the path and file name of the malware file:
"winrpc.exe %1"
If the data is the malware file, right-click Default and select Modify to change its value.
In the Value data input box, delete the existing value and type the default value: %SysDir%\NOTEPAD.EXE %1
Click OK.
Close Registry Editor.
Removing Autostart Entries from System Files
Malware autostart entries in system files must be removed before the system can be restarted safely.
Open WIN.INI. To do this, click Start>Run, type WIN.INI, then press Enter.
Under the [windows] section, locate and delete the file name of the malware file, RAVMOND.EXE, from the following line:
Run=%System%RAVMOND.exe
*Where %System% is the Windows system folder, which is usually C:\Windows\System on Windows 9x and ME, C:\WINNT\System32 on Windows NT and 2000, or C:\Windows\System32 on Windows XP.)
Close WIN.INI and click Yes when prompted to save.
NOTE: If you were not able to terminate the malware process from memory, as described in the previous procedure, restart your system.
Disabling Malware Service For Windows NT, 2000, and XP
Restart your machine to terminate the malware service. Next, remove the malware service from the registry.
Open Registry Editor. To do this, click Start>Run, type REGEDIT, then press Enter.
In the left panel, double-click the following:
HKEY_LOCAL_MACHINE>SYSTEM>CurrentControlSet>
Services>Windows Management Instrumentation Driver Extension
Right click "Windows Management Instrumentation Driver Extension" and select "Delete".
In the left panel, double-click the following:
HKEY_LOCAL_MACHINE>SYSTEM>CurrentControlSet>
Services>NetMeeting Remote Desktop (RPC) Sharing
Right click "NetMeeting Remote Desktop (RPC) Sharing" and select "Delete".
In the left panel, double-click the following:
HKEY_LOCAL_MACHINE>SYSTEM>CurrentControlSet>
Services>Microsoft NetWork FireWall Services
Right click "Microsoft NetWork FireWall Services" and select "Delete".
Close Registry Editor.
Additional Windows ME/XP Cleaning Instructions
Windows Millennium Edition (ME) and Windows XP have a feature known as System Restore, which creates backups of certain files in the _Restore folder. The System Restore feature usually backs up files with EXE or COM extensions, which may include infected files and malware programs. Files in the _Restore folder are protected and can only be accessed using System Restore. This feature must be disabled first before Trend Micro antivirus can access and clean these files.
The following procedure disables the System Restore feature:
For Windows ME
Right-click the My Computer icon on the Desktop and click Properties.
Click the Performance tab.
Click the File System button.
Click the Troubleshooting tab.
Select Disable System Restore.
Click Apply > Close > Close.
When prompted to restart, click Yes.
Press F8 while the system restarts.
Choose Safe Mode then hit the Enter key.
After your system has restarted, continue with the scan/clean process. Files under the _Restore folder can now be deleted.
Re-enable System Restore by clearing Disable System Restore and restarting your system normally.
For Windows XP
Log on as Administrator.
Right-click the My Computer icon on the desktop and click Properties.
Click the System Restore tab.
Select Turn off System Restore.
Click Apply > Yes > OK.
Continue with the scan/clean process. Files under the _Restore folder can now be deleted.
Re-enable System Restore by clearing Turn off System Restore
AUTOMATIC REMOVAL INSTRUCTIONS
To automatically remove this malware from your system, please refer to the Trend Micro Damage Cleanup Engine and Template.
MANUAL REMOVAL INSTRUCTIONS
Identifying the Malware Program
To remove this malware, first identify the malware program.
Scan your system with your Trend Micro antivirus product.
NOTE all files detected as WORM_LOVGATE.G.
Trend Micro customers must download the latest pattern file before scanning their system. Other Internet users may use Housecall, Trend Micro’s free online virus scanner.
Terminating the Malware Program
This procedure terminates the running malware process from memory. If the process name is not known, you will need the name(s) of the file(s) detected earlier.
Open Windows Task Manager.
On Windows 95/98/ME systems, press
CTRL+ALT+DELETE
On Windows NT/2000/XP systems, press
CTRL+SHIFT+ESC, then click the Processes tab.
In the list of running programs*, locate the malware file or files detected earlier.
Select the file, then press either the End Task or the End Process button (depending on the version of Windows on your system).
Do the same for all detected malware files in the list of running processes.
To check if the malware process has been terminated, close Task Manager, and then open it again.
(Terminating an instance of the malware will also launch an instance of IEXPLORE.EXE. Terminate all other instances first before terminating IEXPLORE.EXE.)
Close Task Manager.
*NOTE: On systems running Windows 95/98/ME, Task Manager may not show certain processes. You may use a third party process viewer to terminate the malware process. Otherwise, continue with the next procedure, noting additional instructions.
Removing Autostart Entries from the Registry
Removing autostart entries from the registry prevents the malware from executing during startup.
Open Registry Editor. To do this, click Start>Run, type REGEDIT, then press Enter.
In the left panel, double-click the following:
HKEY_LOCAL_MACHINE>Software>Microsoft>Windows>
CurrentVersion>Run
In the right panel, locate and delete the following entries:
WinHelp = "C:\WINNT\System32\WinHelp.exe"
WinGate initialize = "C:\WINNT\System32\WinGate.exe -remoteshell"
Remote Procedure Call Locator = "RUNDLL32.EXE reg678.dll ondll_reg"
Program In Windows = "C:\WINNT\System32\IEXPLORE.EXE"
In the left panel, double-click the following:
HKEY_CURRENT_USER>Software>Microsoft>WindowsNT>
CurentVersion>Windows
In the right panel, locate and delete the following entry:
Run = ”RAVMOND.EXE”
Addressing Registry Shell Spawning
Registry shell spawning executes the malware when a user tries to run an .TXT file. The following procedures should restore the registry to its original settings.
Still in Registry Editor, in the left panel, double-click the following:
HKEY_CLASSES_ROOT>txtfile>shell>open>command
In the right panel, locate the registry entry:
Default
Check whether its data (in the rightmost column) is the path and file name of the malware file:
"winrpc.exe %1"
If the data is the malware file, right-click Default and select Modify to change its value.
In the Value data input box, delete the existing value and type the default value: %SysDir%\NOTEPAD.EXE %1
Click OK.
Close Registry Editor.
Removing Autostart Entries from System Files
Malware autostart entries in system files must be removed before the system can be restarted safely.
Open WIN.INI. To do this, click Start>Run, type WIN.INI, then press Enter.
Under the [windows] section, locate and delete the file name of the malware file, RAVMOND.EXE, from the following line:
Run=%System%RAVMOND.exe
*Where %System% is the Windows system folder, which is usually C:\Windows\System on Windows 9x and ME, C:\WINNT\System32 on Windows NT and 2000, or C:\Windows\System32 on Windows XP.)
Close WIN.INI and click Yes when prompted to save.
NOTE: If you were not able to terminate the malware process from memory, as described in the previous procedure, restart your system.
Disabling Malware Service For Windows NT, 2000, and XP
Restart your machine to terminate the malware service. Next, remove the malware service from the registry.
Open Registry Editor. To do this, click Start>Run, type REGEDIT, then press Enter.
In the left panel, double-click the following:
HKEY_LOCAL_MACHINE>SYSTEM>CurrentControlSet>
Services>Windows Management Instrumentation Driver Extension
Right click "Windows Management Instrumentation Driver Extension" and select "Delete".
In the left panel, double-click the following:
HKEY_LOCAL_MACHINE>SYSTEM>CurrentControlSet>
Services>NetMeeting Remote Desktop (RPC) Sharing
Right click "NetMeeting Remote Desktop (RPC) Sharing" and select "Delete".
In the left panel, double-click the following:
HKEY_LOCAL_MACHINE>SYSTEM>CurrentControlSet>
Services>Microsoft NetWork FireWall Services
Right click "Microsoft NetWork FireWall Services" and select "Delete".
Close Registry Editor.
Additional Windows ME/XP Cleaning Instructions
Windows Millennium Edition (ME) and Windows XP have a feature known as System Restore, which creates backups of certain files in the _Restore folder. The System Restore feature usually backs up files with EXE or COM extensions, which may include infected files and malware programs. Files in the _Restore folder are protected and can only be accessed using System Restore. This feature must be disabled first before Trend Micro antivirus can access and clean these files.
The following procedure disables the System Restore feature:
For Windows ME
Right-click the My Computer icon on the Desktop and click Properties.
Click the Performance tab.
Click the File System button.
Click the Troubleshooting tab.
Select Disable System Restore.
Click Apply > Close > Close.
When prompted to restart, click Yes.
Press F8 while the system restarts.
Choose Safe Mode then hit the Enter key.
After your system has restarted, continue with the scan/clean process. Files under the _Restore folder can now be deleted.
Re-enable System Restore by clearing Disable System Restore and restarting your system normally.
For Windows XP
Log on as Administrator.
Right-click the My Computer icon on the desktop and click Properties.
Click the System Restore tab.
Select Turn off System Restore.
Click Apply > Yes > OK.
Continue with the scan/clean process. Files under the _Restore folder can now be deleted.
Re-enable System Restore by clearing Turn off System Restore
Попробуй Microsoft AntiSpyware или в локалке -
Проделал все. В трее теперь IEXPLORER.EXE не сидит (токо маленькими буквами в реестре и WIN.INI лишних строк нет, как и файлов подозрительных в системной паке.
НО! При каждом ФУЛЛ-СКАНЕ Нортон антивирус находит в компе три зараженных файла, не может их стереть (см. картинку) и говорит: ВАШ комп все еще заражен
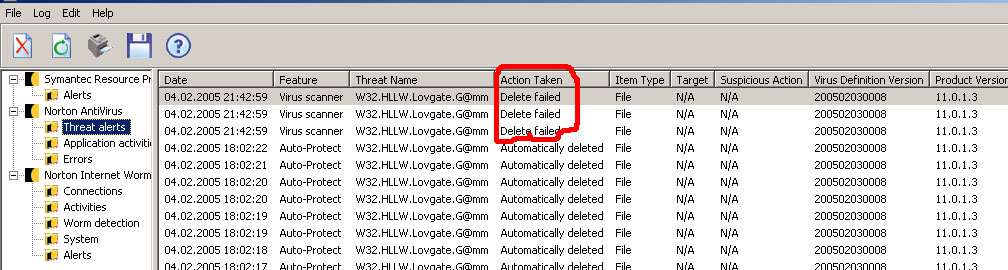
НО! При каждом ФУЛЛ-СКАНЕ Нортон антивирус находит в компе три зараженных файла, не может их стереть (см. картинку) и говорит: ВАШ комп все еще заражен

www.trendmicro.com
Там Virus Encyclopedia
или еще какая нить база вирусов
Там подробно расписано, какие вирусу принадлежат процессы, и где он в реестре прописывается... Собственно снимаешь енти процессы и сканируешь Nortonom
Там Virus Encyclopedia
или еще какая нить база вирусов
Там подробно расписано, какие вирусу принадлежат процессы, и где он в реестре прописывается... Собственно снимаешь енти процессы и сканируешь Nortonom
Оставить комментарий
Fowler
Нортон антивирус нашел вирус - он постоянно удаляет тмпшники, которые тот генерит.